Certification Presentation Options
Certifications can show effective permissions, details for one intermediate type, or a summary of how access is derived including policies, roles, and groups.
Effective and system permissions
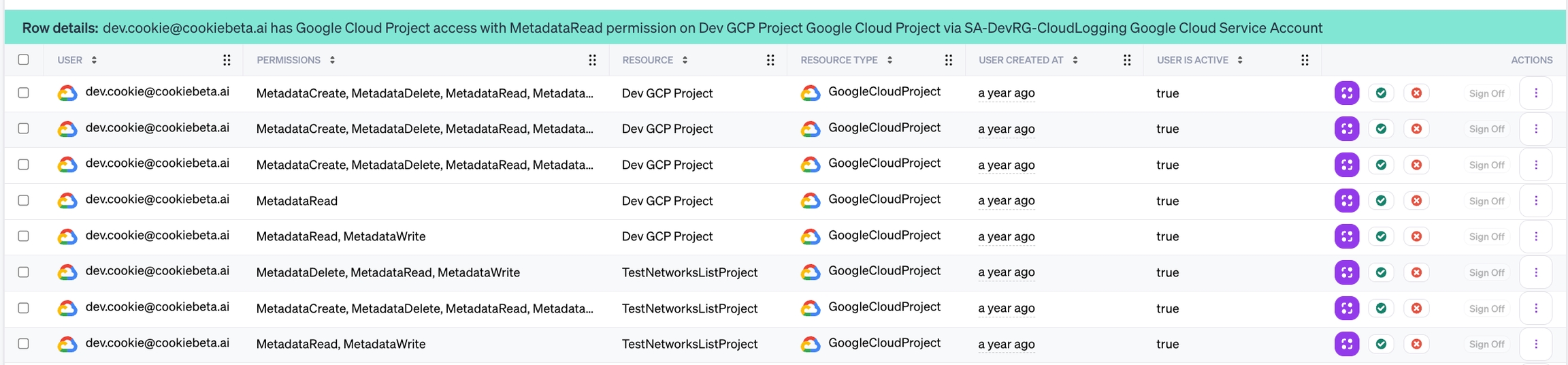
Depending on the Workflow Query Mode, reviewers will certify the combined effective Permissions for each result, or the Summary of access and System Permissions for each result. The Permissions column will be empty when reviewing certifications that use system-mode queries. Instead, an optional column lists System Permissions.
Show intermediate relationship
For workflows specifying a Relationship entity category, certification rows represent connections from one entity to another, by way of the related intermediate entity. For example, AWS IAM User to AWS S3 Bucket with AWS IAM Role for the Relationship will return rows with unique connections of User connected by Role (or directly) to an S3 Bucket. A query can specify only one Relationship.
These certifications will include optional columns showing the properties of the related entity, populated whenever an entity of the chosen category exists in a results authorization path. For example, when choosing a Role for the Relationship to show, certifications will include filterable and sortable Intermediate Role columns.
This option can be preferable when a multi-entity summary of access is more information than reviewers require.
Summary entities
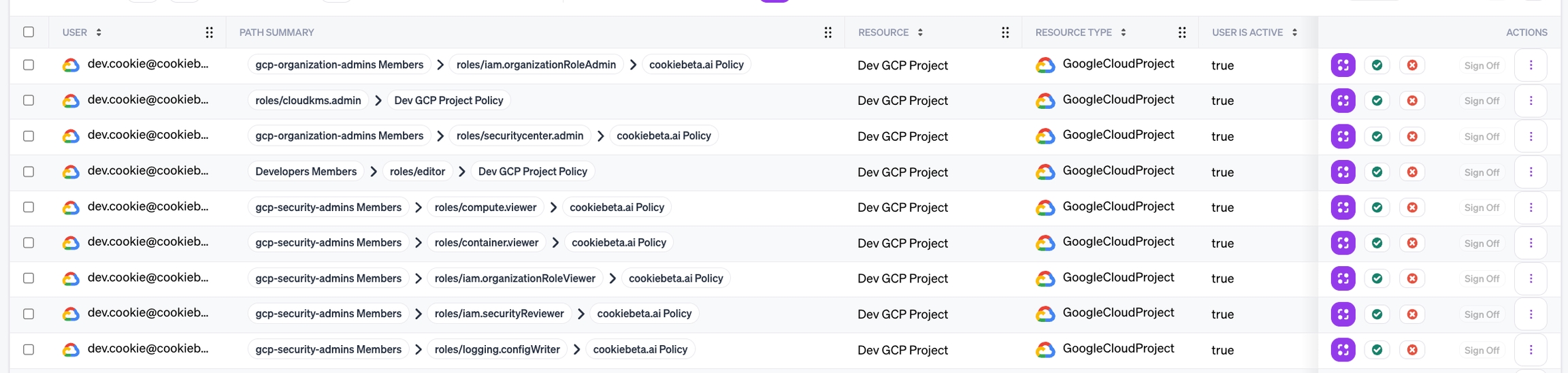
Selecting Summary Entities is similar to selecting an intermediate Relationship, except that several entity types are selectable at once. When included in a workflow query, the certification results will be entities of the source category with a relationship of the destination category, and will include a summary of the path that made the connection.
The entity types selected as Summary Entities for the query appear in the summary column. For example, a query from User to Bucket with a summary including Group and Role will return all the unique results of Users connected to Buckets, along with a summarized path. The summarized path might be GroupA -> Role1, or just Role2 (if no groups are in the path). If the user has direct access to a bucket (not by way of group or role), the summary will be empty.
Workflows that use System mode in combination with Summary Entities will not include effective permissions calculations (the "Permissions" certification column will be empty). Instead, users will be able to review the "System Permissions" and "Summary Entities" columns for their assigned results.
By inspecting the relationships between intermediate entities and the resulting system permissions, certification reviewers can certify how access is actually configured for identities within an organization:
For example, for a well-managed Google organization, the authorization path will typically include roles bound to groups that a principal is a member of. However, the access summary indicates possible issues — such as when a policy is directly attached to the resource it grants permissions on, and when permissions are not granted by group assignment.
Generating the summary can add additional time to certification creation, and summaries can contain a limited number of total entities:
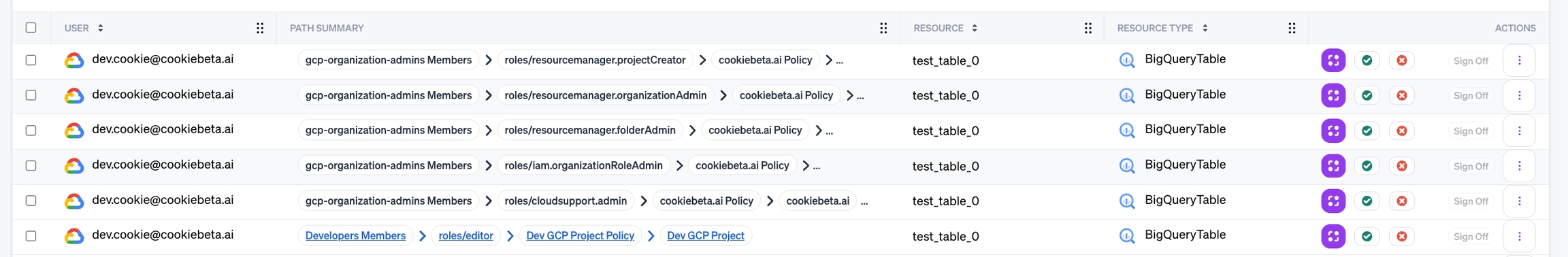
Path Summaries that contain too many nodes will have a placeholder (
...) indicating the missing intermediate entities.Summary details for these results will indicate that additional nodes exist, but are not shown.
Examples
Path summaries are a Workflows visualization option that can be especially useful for understanding role-based access controls for providers such as Azure and Google Cloud. Choosing Summary Entities when creating a workflow enables reviewers to judge whether the configured permissions are appropriate based on security policies, including:
If permissions are granted by group or role membership, or direct assignment
The name of the role or group granting permissions
The objects policies apply to, such as the query destination resource (for directly-applied policies) or an upper-level resource in the resource hierarchy (for inherited policies)
For Google Groups, the kind of membership (such as
ownerormember)
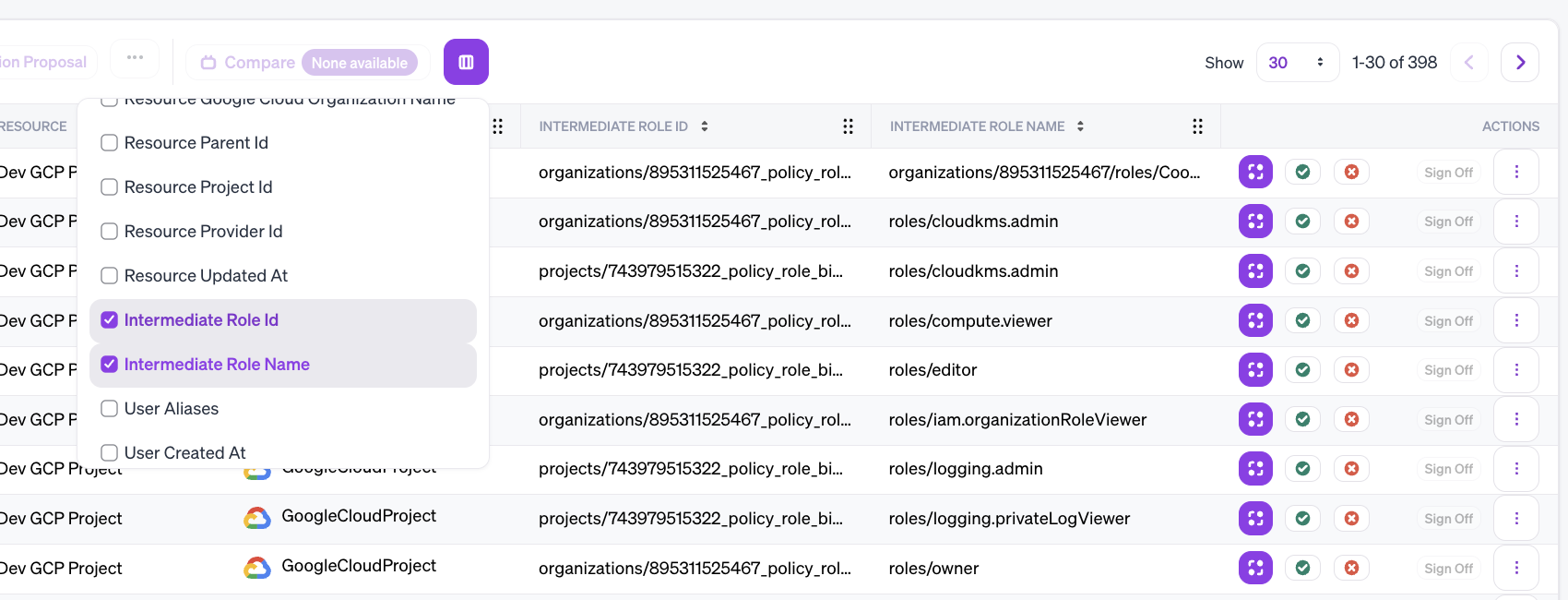
To add and customize the access summary when creating a workflow, specify the source and destination entity, expand Advanced Options, and pick the Summary Entities you want visible to reviewers. To only return results with paths containing or excluding a specific entity, use the Requires or Excludes Entity Types filter.
Possible entities for the summary depend on the provider and the search mode. When searching Google User to Google Cloud Project, options include:
Google Cloud Folder
Google Cloud IAM Policy
Google Cloud Role Binding
Google Cloud Organization
Google Service Account
Google Service Account Role Binding
Google Group
Google Group Membership
If an expected entity type is not in the list of summary entities, ensure the query uses System mode, and that the entity type is not Excluded.
Policy inheritance and resource hierarchy
A Google Cloud organization has a hierarchical structure of folders containing projects, which contain individual services. A policy applied at the organization applies to all resources beneath it. Projects and services within a folder likewise inherit policies on that folder. See here for more information on search for directly-applied policies.
To create a query that returns results with any access, but including a summary column indicating where in the resource hierarchy the permissions apply:
Create a workflow, and enable System mode
Pick the source and destination (Google User to Big Query Table)
Expand Advanced Options > Summary Entities
Pick the entity types Folder, Organization, Project, IAM Policy, Role Binding, and Group Membership
Finish customizing the workflow and save it
Certifications on this workflow will include a Path Summary column that indicates where a group, policy binding, or role exists in each result's authorization path. Reviewers can click on a role's name to verify the exact resource it is bound to. Reviewers can click an entity name to view more details.
Attribute filters on related entity properties
By adding an attribute filter on an entity property such as name, is_active or department, you can create workflows that only include results for source, destination, and related entity types with matching attributes. A workflow query might use such filters to review access for a specific group or role (Group name CONTAINS "developers").
When applying an attribute filter on a required related entity, the following behavior applies:
Attribute filter on Role: only the paths whose Roles meet the constraint appear in the Path Summary column.
Attribute filter on Group: only the paths whose Groups meet the constraint appear in the Path Summary column.
Last updated