Access Remediation (Early Access)
Request authorization changes for certification results
Early Access: Remediation Proposals for Veza Workflows requires support to enable. Please contact your Veza customer success team for more details.
When reviewing a certification, Veza users can submit Remediation Proposals for supported results. When they do, the request is sent to a configured 3rd-party app or email destination, including instructions to remove access and details about potential side effects.
Veza administrators and operators can review and track all requests from the Remediation>Proposals overview.
Optionally, requests can be published with custom webhooks. As Veza does not request write access to connected integrations, webhooks enable a listener running in your own environment to alter role assignments, group memberships, policy statements, or take other privileged actions.
See the following sections for more details:
Limitations
Access remediation is currently possible for Snowflake and Custom Application and Identity Provider users and roles. Remediation Proposals are available for workflows that query:
Source Snowflake Local User to destination Snowflake Database, Table, or View
Source Custom User to destination Custom Resource
the Remediation Proposal button is disabled in certification view when remediation is not supported for the source-destination pair.
As steps to remediate access for custom applications will depend on the provider, you can customize instructions with an API.
Requesting remediation
To request access removal:
Open a valid Certification. The original workflow query must specify source and destination entity types supported for access removal.
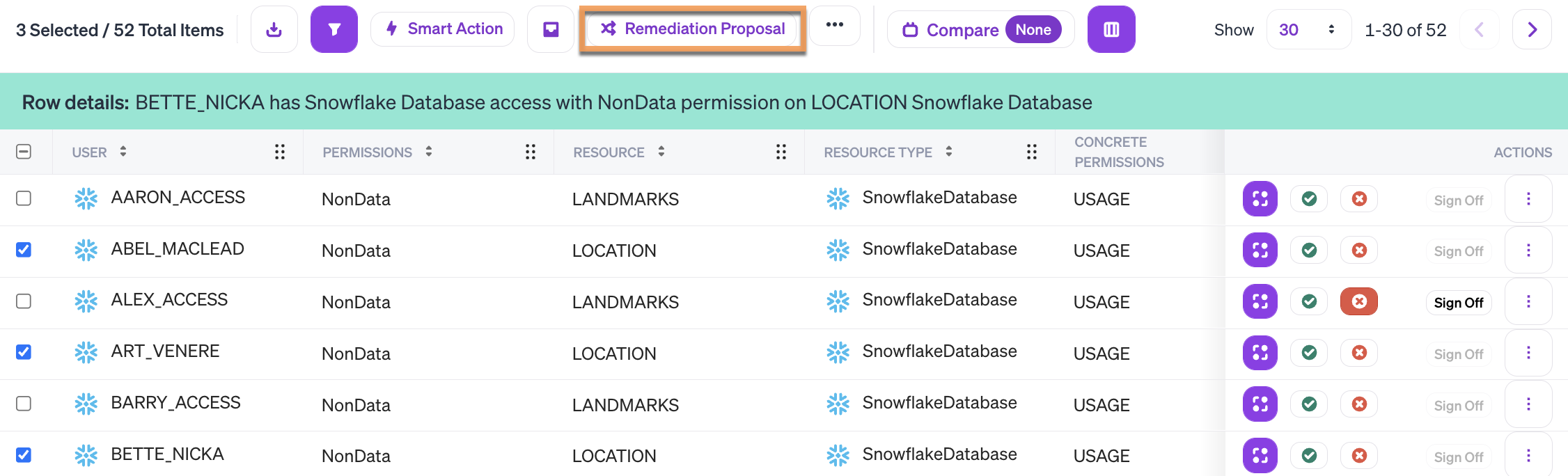
Choose one or more results to request changes for.
Click "Remediation Proposal" on the action bar.
You can request changes for several users at a time, but only if the destination resource is the same for all users.
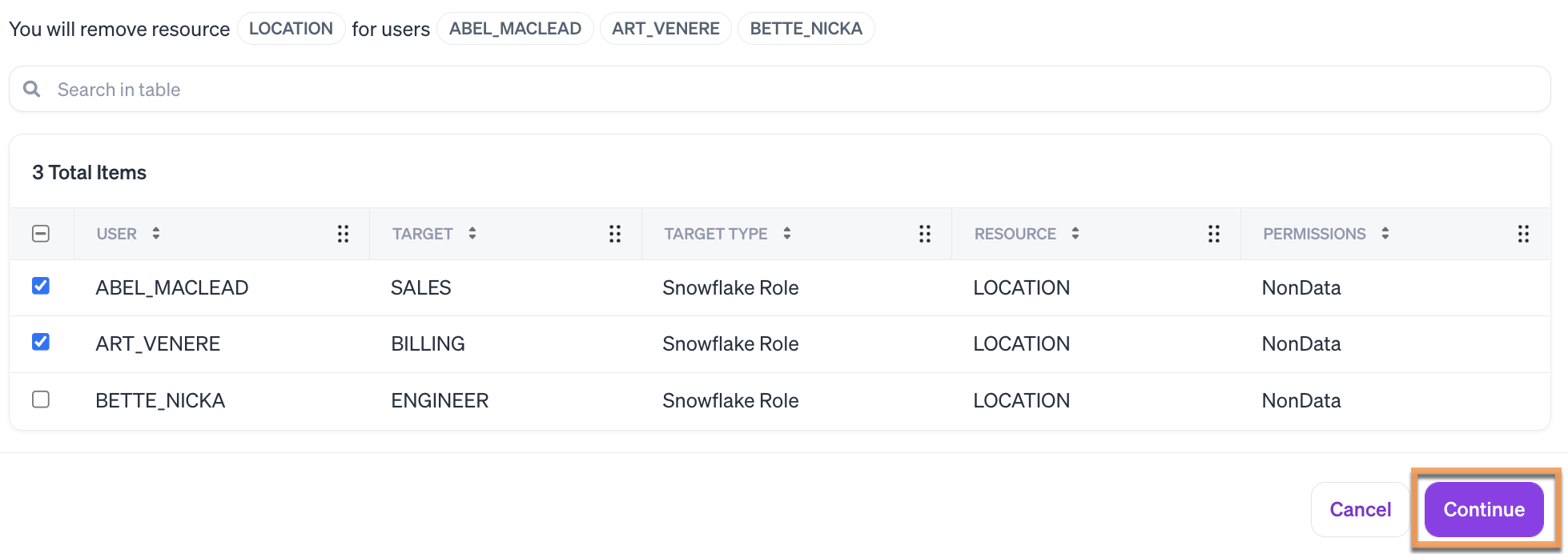
A modal will list the affected users. For each user, you can preview the targeted role to remove, and the resources and permissions allowed by the role .
You can make adjustments to this list with the checkboxes. Click Continue to save your choices.
The Target is the entity (group or role) enabling access to the resource.
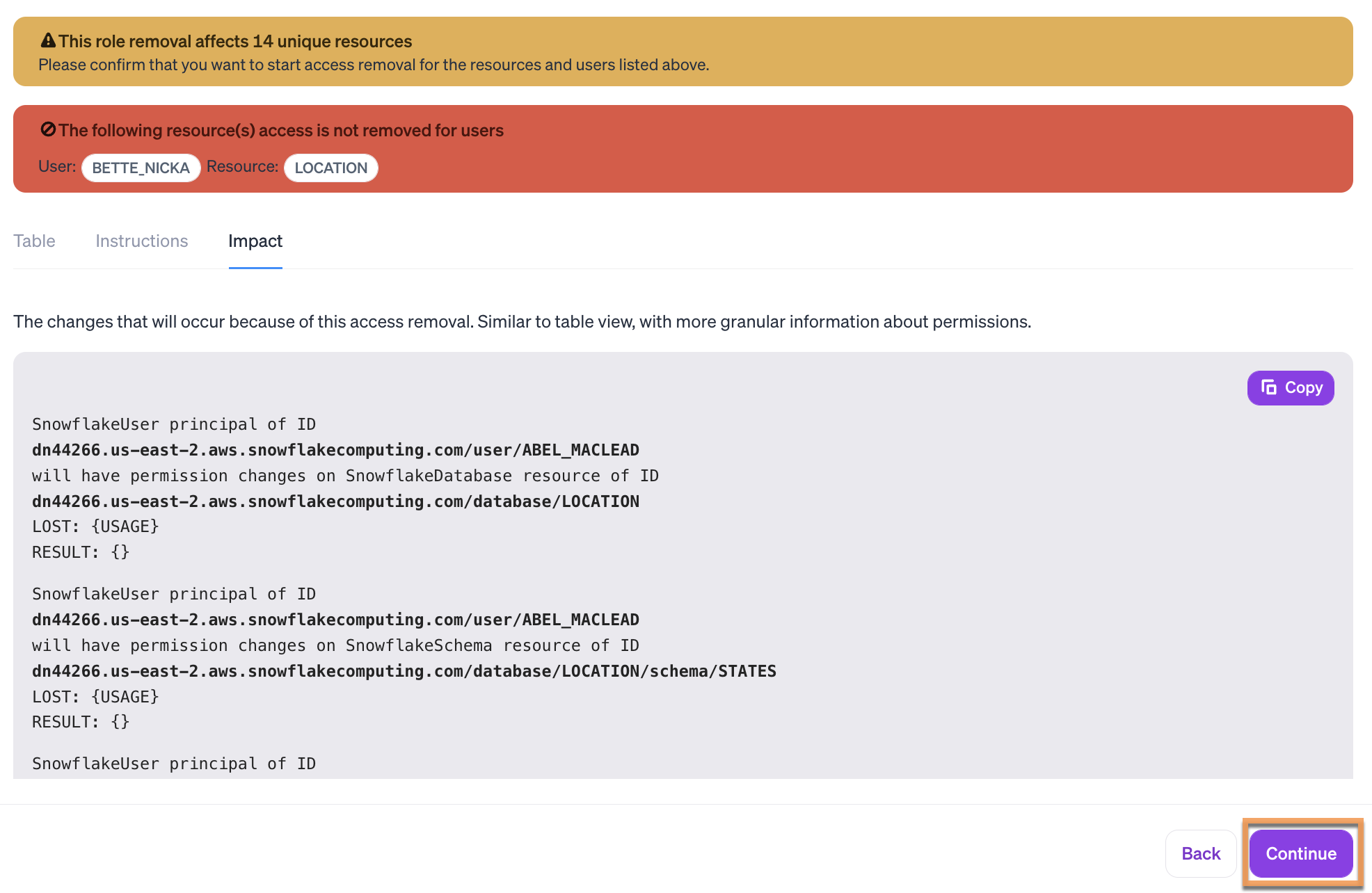
Note that removing access to one resource might change permissions on other resources. Preview the impact of the changes with the Table, Instructions, and Impact tabs.
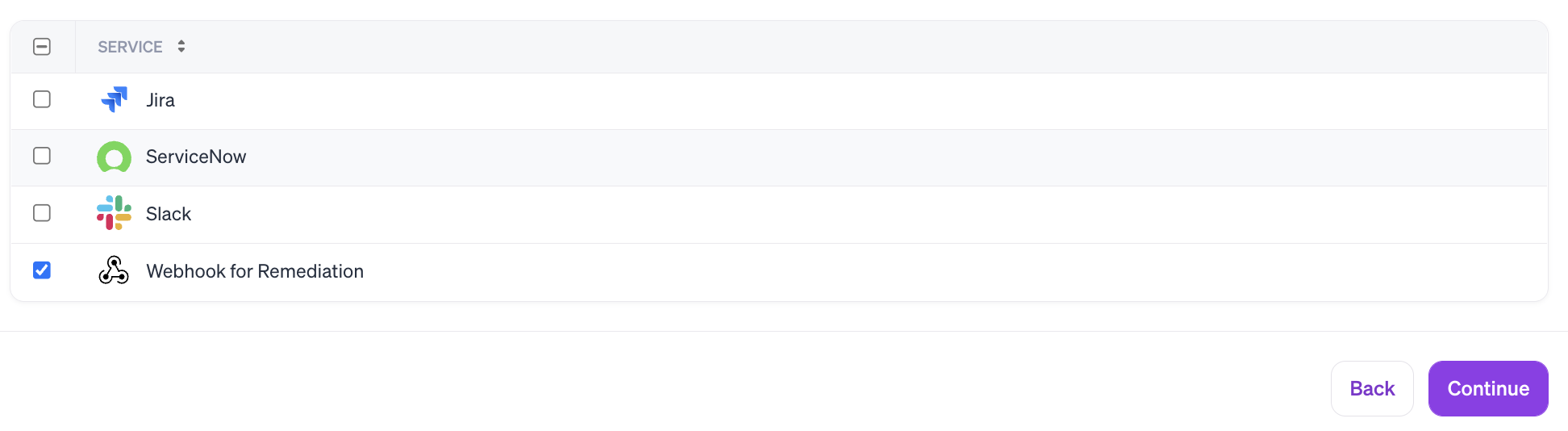
Click Continue to pick a destination from connected Integrations. This could be an email, Slack, or a custom webhook configured to automatically fulfil the request.
Click Send again to confirm and submit the request.
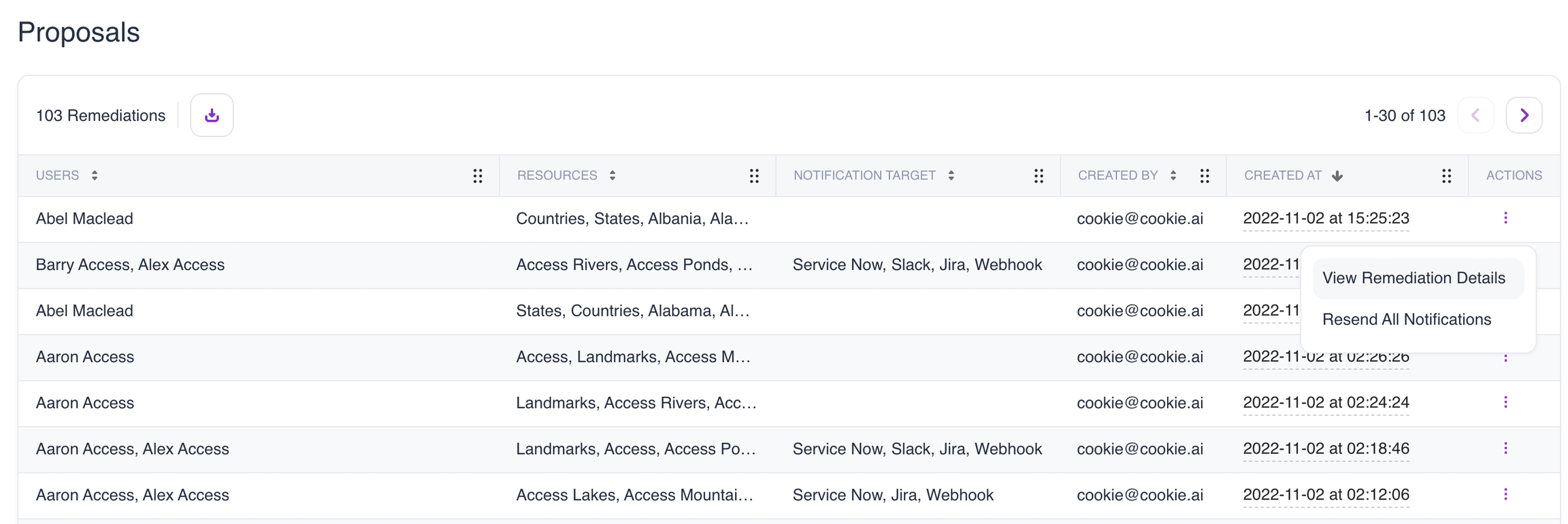
Reviewing remediation proposals
Administrators and Operators can use the Remediation > Proposals panel to review all requests that have been created, sorted by created date by default. The notification target shows the external destination the request was published to.
For each proposal, responders can:
View details, including a list of requested changes, instructions, and the potential impact of the change.
Resend the message to the original target.
See webhooks for an example payload.
Adding instructions for Custom Apps and Identity Providers
As the exact steps to change access within a given application can vary, Veza administrators can add custom instructions for any apps added with Open Authorization API used by their organization. If no template instructions are available, remediation proposals for Custom Application Users and Resources will not include specific instructions.
To customize instructions, add templates with the Custom Instructions API. You can upload one or more templates for each Custom App or Identity Provider.
When users request remediation, Veza will use the template for the matching source and destination pair, and optionally matching properties such as the "provider name" on the source Custom User. The additional property matchers are useful if you have more than one custom app, but different remediation steps for each provider
For example:
Last updated